I was recently asked to code review a friend’s first Laravel app, and when I cloned the repository from GitHub I immediately noticed a few big, red flags. Many of these were common mistakes, so I thought I’d take a moment to discuss how we can safely handle credentials and/or sensitive information in our Laravel applications.
Tag: Security

CodeMash 2013 was my first big tech conference, and since then I’ve only missed two years of the conference. I’ve also been privileged enough to speak at CodeMash 2017 and again last year. Those are just a few of the reasons I’m thrilled to announce that I’ll be speaking again this year at CodeMash 2020!
This year is especially exciting, as I’ll be giving my first KidzMash talk!
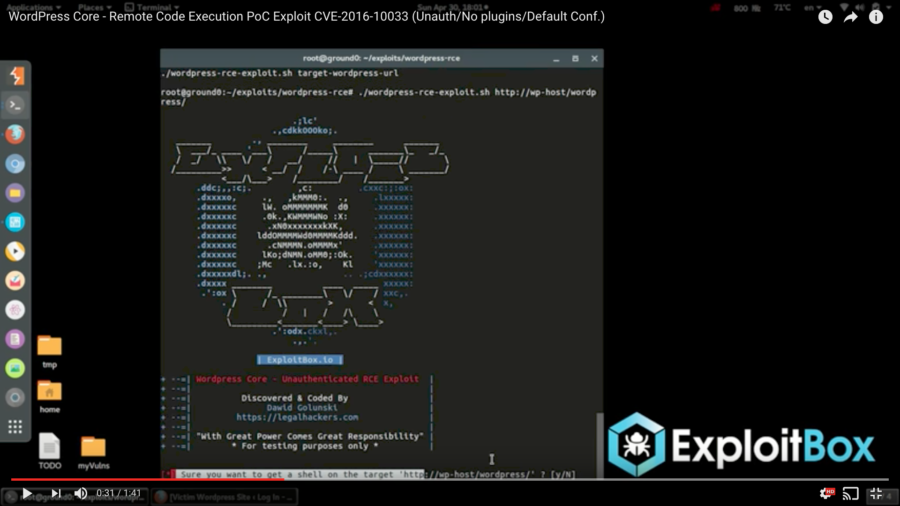
A few days ago, a YouTube video was passed around a few Slack teams I’m a member of showing a proof of concept of an unauthenticated remote code execution vulnerability in WordPress core (in other words, a way for people to execute arbitrary code on your server, which is obviously bad). The video, posted by Dawid Golunski of Legal Hackers, purported that the vulnerability was exploited against a clean installation of WordPress with no plugins and only the default configuration.
This morning, Dawid’s new site, ExploitBox, posted details about the vulnerability. In short, by spoofing a request’s “Host” header, it’s possible to trick WordPress into sending a password reset email with a return path pointing to a domain you control.
The author goes on to hypothesize that if an attacker were to first overload the target’s inbox with large messages (effectively filling it to the point that it couldn’t hold more messages), this would cause the mail host to “bounce” (reject) the message, returning it to the sender (the attacker). Assuming the returned email contained the body of the original message, the attacker now has the link that will allow them to change the user’s password.
As I write this, my new Epiphone Casino is sitting in my lap and I’m looking up George Harrison guitar tabs. Unfortunately, when you’re best known as one of the Fab Four, lawyers love to block access to your work that doesn’t bring in royalty checks for your estate. When looking for one song in particular, What is Life, my go-to tab site, Ultimate-Guitar.com, came up short.
I’ll be giving two talks at the inaugural php[world] conference, organized by the php[architect] team this fall in Washington, D.C. I’m humbled to be speaking alongside a bunch of great developers, including WordPress Lead Developer Andrew Nacin and Taylor Otwell, the creator of Laravel.
Learn how to lock down your WordPress site in this talk based on my blog post on WordPress security basics. This talk covers password strength, the risks of third-party extensions, user management, and securing your wp-config.php file.
Learn how to lock down your WordPress site in this talk based on my blog post of the same name. This talk covers password strength, the risks of third-party extensions, user management, and securing your wp-config.php file.
Each year thousands of websites are hacked. Sometimes it’s by way of a crafty social engineer (someone who tricks someone into giving up information without realizing it) conning some unsuspecting user out of his/her login. Other times it’s a backdoor in some code that grants a malcontent access to a site.
If your site is running on WordPress you can rest easy – WordPress core is considered to be a very secure application. The downside to WordPress core being secure is that if someone breaks into your site you likely have nobody but yourself to blame. Never fear: these tips will help keep your site safe and sound.
For those of you in the Columbus, OH area I’ll be presenting at this month’s Columbus WordPress Meetup on June 18, 2013 (a.k.a. tomorrow). The presentation is based on my latest blog post, WordPress Security Basics, and should be a good high-level introduction to WordPress security.




