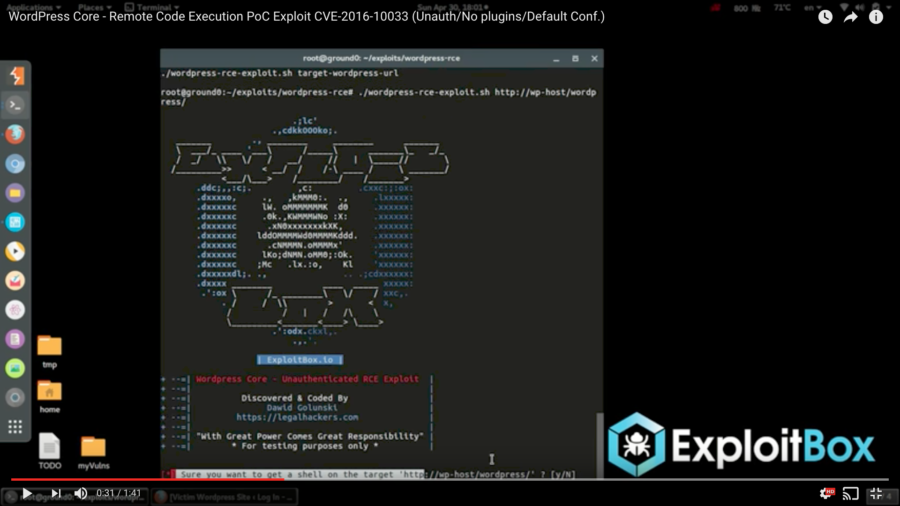
A few days ago, a YouTube video was passed around a few Slack teams I’m a member of showing a proof of concept of an unauthenticated remote code execution vulnerability in WordPress core (in other words, a way for people to execute arbitrary code on your server, which is obviously bad). The video, posted by Dawid Golunski of Legal Hackers, purported that the vulnerability was exploited against a clean installation of WordPress with no plugins and only the default configuration.
This morning, Dawid’s new site, ExploitBox, posted details about the vulnerability. In short, by spoofing a request’s “Host” header, it’s possible to trick WordPress into sending a password reset email with a return path pointing to a domain you control.
The author goes on to hypothesize that if an attacker were to first overload the target’s inbox with large messages (effectively filling it to the point that it couldn’t hold more messages), this would cause the mail host to “bounce” (reject) the message, returning it to the sender (the attacker). Assuming the returned email contained the body of the original message, the attacker now has the link that will allow them to change the user’s password.