This week a few people in the office got really excited about the Signals app from HubSpot, which lets you see when your emails have been opened and whether or not links have been clicked in your emails. While it’s extremely useful for marketers, project managers, and others who have a vested interest in knowing you’ve read their emails, I’d prefer to be able to read the email at my leisure without having the sender essentially standing over my shoulder to see if I’ve read it. For most people it’s not a big concern, but it is incredibly simple to thwart if you’d like a little more privacy in your inbox.
Understanding tracking pixels
The whole thing works through a little transparent image known in the marketing world as a tracking pixel; this resource, usually a 1×1 transparent image, is embedded in the email with a series of query string arguments and might look something like this:
|
1 2 3 4 |
<img style="display: none;" alt="" src="//mytrackingdomain.tld/track.png?msgId=123" data-mce-src="//mytrackingdomain.tld/track.png?msgId=123" data-mce-style="display: none;"> |
When that image is requested, a HTTP GET request is sent to mytrackingdomain.tld to load the image, just like loading an image on any other webpage. The tracking domain sees that a request for /track.png?msgId=123 has come in, and can then associate the “msgId” argument with a message, newsletter campaign, etc. that the tracker knows about. For instance, if Sarah sends an email with Brad that includes a tracking pixel, the tracking app assigns that message an ID and, upon that pixel being requested, Sarah gets notified that Brad has opened the email. Trackers can also count the number of requests for that particular URI, enabling Sarah to see how many times Brad has opened the email.
Who else is using them?
Signals is far from the only service using tracking pixels. If you view the raw source of emails from most (if not all) email marketing services you’re sure to find the same idea (that’s how they can calculate your “Open rate” for email campaigns). There are even some site analytics platforms that use this method for tracking site views and basic demographics (see “What can they track?” below).
Tracking links
Another benefit of services like Signals for marketers is the ability to track clicks on links within the emails. Just like with tracking pixels, Signals is far from being the only one doing this; most email marketing services use this same trick so they can gather information about a click before redirecting the user to their intended location. Search engines like Google even use tracking links so they can see what links are getting clicked; take a look at the actual URL we’re being taken to before getting to the homepage of this site:
![]()
Rather than simply linking to http://stevegrunwell.com, Google is injecting a tracker into the link, enabling them to see things like the user’s search query, browser data, and more. URL shorteners that offer analytics use a similar trick, but don’t have to be as sneaky about it as the user is already knowingly clicking through to the shortener on his/her way to the destination site.
What can they track?
A simple GET HTTP request from a browser looks something like this (you can try it for yourself by opening Chrome’s Web Inspector and going to the “Network” tab):
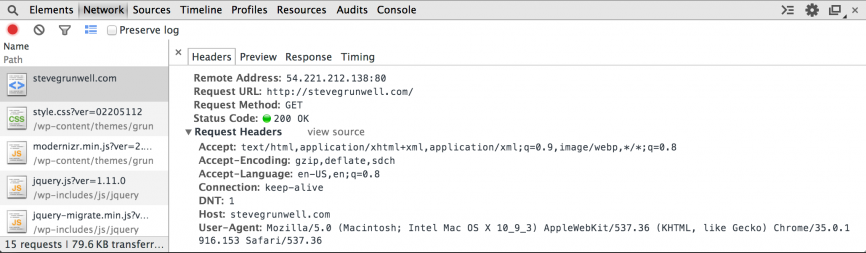
Some of these are pretty standard, but a few items can be used by marketers to gain information about me:
My language
The Accept-Language header tells them that my computer is configured to accept the United States’ form of English. Not a big deal if I’m visiting sites with content written in English, but if marketers see, for instance, a large number of German readers they might decide that a German version of the content could be helpful/profitable.
My browser and operating system
The User-Agent header tells the remote server what kind of computer I’m using. The history of user-agent strings is a long, storied, and unnecessarily complicated one, but we’ll gather what we can.
The user-agent string my browser sent was: “Mozilla/5.0 (Macintosh; Intel Mac OS X 10_9_3) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/35.0.1916.153 Safari/537.36”
This essentially tells every server I request content from that I’m running an Intel-based Mac running OS 10.9.3 (Mavericks), using Google Chrome version 35.0.1916.153, the current release as of this writing. Marketers can parse this information and make assumptions: if this isn’t a work computer, I’ve at least at some point had enough money to afford a Mac, and I’m using Chrome rather than Safari so I likely know at least enough about computers to install a different browser. Marketers might build a very different profile of me than they would someone whose user-agent string indicated that the user was running Windows XP with Internet Explorer 7, for instance.
My location
Without getting into the nitty-gritty details of IP block assignments, in many cases your IP address can be used to roughly determine where you’re coming from. Using tools like What Is My IP you can typically see basic information about the location of a user based solely on his/her IP address. In my case, it shows that I’m on a residential Time Warner Cable IP address in Columbus, OH, which is 100% correct.
It’s worth noting that IP addresses, user-agent strings, and more can be spoofed, so these are not 100% reliable metrics when collecting data about users, though for most situations it’s close enough for jazz. People concerned with their privacy often take measures to alter this information, but most of it could be considered harmless enough for day-to-day traffic.
Circumventing Signals tracking
Now that we understand tracking pixels and URLs, what can we do to make sure that marketers won’t know when we’ve opened an email? You’ll be surprised how easy it can be!
First, inspect the source of an email that’s using these features to determine the domain used for tracking (hopefully it’s a tracking-specific domain, as you wouldn’t want to block a legitimate CDN or other host that you actually want to load content from). In the case of Signals, the tracking pixel URL looks something like:
http://t.signauxtrois.com/img.gif?ukey={key}&key={another_key}
The important thing to note here is the domain: “t.signauxtrois.com”. Next, open up your hosts file (/etc/hosts on *nix-based operating systems, /system32/drivers/etc/hosts on Windows; you’ll need root or administrator privileges, respectively) and add the following entry (If you’re having trouble, this article on editing hosts files may help):
|
1 |
127.0.0.1 t.signauxtrois.com |
Save the file and boom, no more tracking! Basically what we’ve accomplished is told our computer “take any requests for t.signauxtrois.com and route them to my own machine”, meaning your computer can’t talk to the tracker unless you remove the rule from your hosts file. See, wasn’t that simple?
Caveats and warnings
I take no issue with blocking tracking on marketing emails, but you’ll want to make sure you’re careful when attempting to block other sites. Google’s tracking links, for instance, would be a bad thing to try to circumvent with a hosts file entry as suddenly Google would stop working on your computer due to Google tracking clicks through google.com instead of a sub-domain.
There’s also a possibility that tracking links will stop functioning as normal links, meaning you might have to actually view the source to get the intended URL. For those developmentally-inclined, you might write a script running on your local machine at the blocked hostnames that resolves the tracking URL without tracking (but that’s a blog post for another day).
Wrapping up
Hopefully you’ve at least learned a little bit more about how to protect your privacy where tracking pixels and URLs are involved and/or found a way to keep that co-worker from keeping tabs on you. If you have stories about tracking pixels or URLs, are an angry marketer, or have anything else to add please leave a comment!




Adam Chauvin
How do i determine what the pixel URL is when using outlook to manage e-mails? I looked at the properties of the e-mail, recipient, etc. but I cannot find a URL that looks similar to your example.
I do see a lot of things that look like GUIDs all over the place though.
Steve
It would be hard to tell without seeing the exact email in question, but tracking pixels can come in all shapes and sizes, including legitimate images (e.g. a company logo passing a query string argument could be used to track email opens) so anything with a GUID might be suspect. That’s the tough thing about trying to circumvent these: it’s easy for marketers to change them, and then we’re back to square one.